Centralized Configuration Management using Azure App Configuration: Using Azure Key Vault Side-by-Side

Centralized Configuration Management using Azure App Configuration Series
- Introduction
- Using Managed Identities to Access Azure App Configuration
- Setting Up Dynamic Refresh for Configuration Values
- Setting Up Offline Caching
- Implementing Custom Offline Cache
- Using Azure Key Vault Side-by-Side (This Article)
- Local Debugging When Using Managed Identities to Access Azure App Configuration
In this article we will look at how we can use Azure Key Vault along side Azure App Configuration in your ASP.Net Core applications. Azure App Configuration and Azure Key Vault services both can act as Configuration providers for .Net Core applications. But Azure App Configuration and Azure Key Vault serves 2 different purposes. You can learn more about Azure App Configuration and How it differs from Azure Key Vault from a previous article in my blog.
Previously Azure App Configuration did not support associating with Azure Key Vault. But now Azure App Configuration supports referencing secrets from Azure Key Vault.
Let’s see how you can use this functionality to combine Azure Key Vault with Azure App Configuration and use all the benefits that Azure App Configuration provides for your applications.
For this example, also we will use the Music Store application we used for the earlier articles as well. But to demonstrate this I am using a simple change to the application that shows a secret value that is fetched from Azure Key Vault. (Not a real-world use case, I know. But demonstrates the usage 😉 )
The value I want to access has the key AppSettings:Identity:Secret and the value needs to be stored in the Key Vault. Let’s see how we can configure this. In the AzureAppConfigurationOptions class you have a method called ConfigureKeyVault() that we can use to associate Azure Key Vault. And since Azure Key Vault supports the use of Managed Identities, you can use the same approach of using Managed Identities to configure Azure Key Vault.
using Azure.Identity;
using Microsoft.Extensions.Configuration.AzureAppConfiguration;
namespace MusicStore.Web
{
public class Program
{
...
public static IHostBuilder CreateHostBuilder(string[] args) =>
Host.CreateDefaultBuilder(args)
.ConfigureWebHostDefaults(webBuilder => {
webBuilder.UseStartup<Startup>();
})
.ConfigureAppConfiguration((context, config) => {
var settings = config.Build();
var appConfigEndpoint = settings["AppSettings:AppConfiguration:Endpoint"];
var userAssignedIdentityClientId = settings["AppSettings:Identity:ClientId"];
if (!string.IsNullOrEmpty(appConfigEndpoint))
{
var endpoint = new Uri(appConfigEndpoint);
config.AddAzureAppConfiguration(options =>
{
options
// Use managed identity to access app configuration
.Connect(endpoint, new ManagedIdentityCredential(clientId: userAssignedIdentityClientId))
// Use managed identity to configure Key Vault
.ConfigureKeyVault(vaultOpt =>
{
vaultOpt.SetCredential(new ManagedIdentityCredential(clientId: userAssignedIdentityClientId));
});
...
});
}
});
}
}In this code segment, we can pass in a AzureAppConfigurationKeyVaultOptions instance into the ConfigureKeyVault() method and in that instance we have SetCredential() method that takes in a TokenCredential instance. So just like we did for Managed Identity access for Azure App Configuration we can pass in a ManagedIdentityCredential instance with the clientId of the User-Assigned Managed Identity we used for the Music Store application. That is all you need to do in the Program.cs file.
To use the secret, we fetched from Key Vault, I have updated the AppSettings class with property of an Identity instance that has a string property called Secret that we are going to bind our configuration.
namespace MusicStore.Shared
{
public class AppSettings
{
public Discount Discount { get; set; }
public Identity Identity { get; set; }
}
public class Discount
{
public double Amount { get; set; }
}
public class Identity
{
public string Secret { get; set; } // <<< Property for the Key Vault secret
}
}And finally, we need to update the _Layout.cshtml to show the secret value in the footer of the Music Store application.
<!DOCTYPE html>
<html lang="en">
...
<footer class="border-top footer text-muted">
<div class="container">
Music Store © 2020 - <a asp-area="" asp-controller="Home" asp-action="Privacy">Privacy Policy</a> | Secret: @Settings.Value.Identity.Secret
</div>
</footer>
...
</body>
</html>That is all we need to do in the application. Next, we need to setup things in the Azure Portal.
Wire-up Azure Key Vault with Azure App Configuration
I’ve created an Azure Key Vault instance with the name of music-store-vault in the Azure Portal. Then I must add the secret value to the Key Vault.
You can use any name for the secret in Azure Key Vault since we will be doing a mapping from Azure App Configuration and the key that is used in the App Configuration is the key that will be used in the application. But for this example, sticking with the conventions I am using the
AppSettings--Identity--Secretas the secret key that follows the conventions for Azure Key Vault.
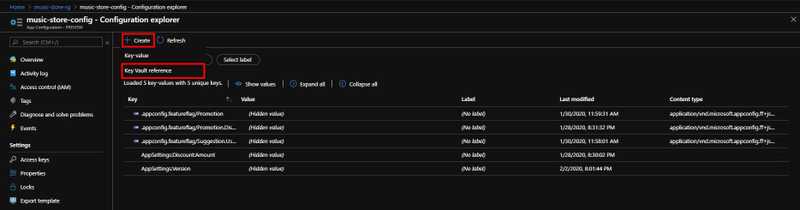
Once you add the secret to the Key Vault, then you need to go to the Azure App Configuration instance and add a Key Vault Reference. Click on the Create link and click on Key Vault Reference link.
In the new blade you can add the Key for the configuration. For us it is AppSettings:Identity:Secret. Then you have the option to Browse fort he secrets value or Input a Secret Identifier. In the Browse tab select the Subscription, the Resource Group and the Key Vault instance in the resource group, then you can select a Secret from that Key Vault instance and finally select from an available Version of the secret. We want to use the latest version.
In the other Input option, you can directly add the Secret Identifier for the given secret. The secret identifier is the URL for the secret.
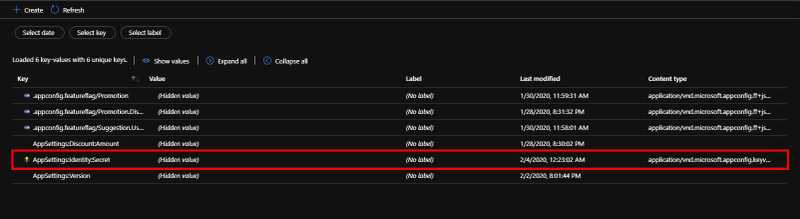
Once you add the key vault reference, you can see the added reference in the list of configuration values available. You can identify the Key Vault references using the Key Icon in front of the config keys.
Since we are using a User-Assigned Managed Identity, we need to add an Access Policy into the Key Vault using the Managed Identity.
Here we are giving get, list and create permissions for Secrets and Certificates and get, list, delete, decrypt, encrypt, wrap, unwrap and create permission for Keys. Depending on the access you need you can change this. And then select the music-store-identity as our User-Assigned Managed Identity.
Once this is done, push your application into Azure App Services and see that the application is running, and the footer of the Music Store app is showing the secret value fetched from Azure Key Vault.
Summary
In this article we looked at how we can use Azure Key Vault as a complementary service along side Azure App Configuration to fetch secrets that is stored in Azure Key Vault in your ASP.Net core application. The code sample is available in the Azure App Configuration Using Azure Key Vault Example GitHub repository. I’ll see you in the next article.
You Might Also Like
← Previous Post
Next Post →