Centralized Configuration Management using Azure App Configuration: Using Managed Identities to Access Azure App Configuration

Centralized Configuration Management using Azure App Configuration Series
- Introduction
- Using Managed Identities to Access Azure App Configuration (This Article)
- Setting Up Dynamic Refresh for Configuration Values
- Setting Up Offline Caching
- Implementing Custom Offline Cache
- Using Azure Key Vault Side-by-Side
- Local Debugging When Using Managed Identities to Access Azure App Configuration
In a previous article we looked at how we can perform Centralized Configuration Management for the Cloud using Azure App Configuration. In that article we had a look at a basic example of fetching configuration settings from Azure App Configuration and how to configure it. In this article and a few follow up articles we’ll look at some other usages of Azure App Configuration.
In the previous example, we were using the Connection String to access Azure App Configuration. This is not the best approach to do so, since it will take your towards adding the connection strings to your source code and you need to manage these credentials yourself. But now you don’t have to do that with Managed Identities for Azure Resources. And Azure App Configuration supports the use of Managed Identities to access App Configuration. You can use both System Assigned Managed Identities and User-Assigned Managed Identities to access Azure App Configuration. Let’s see this in action.
The changes we have done to the Music Store app from the preview Feature Flags for ASP.Net Core series is that we are fetching the discount amount from App Configuration instead of having it hard coded in the application. Allowing us the flexibility to set the discount as per market needs.
Using System Assigned Managed Identity to Access App Configuration
It is simple to add support to use Managed Identities to access App Configuration. If you are using the latest preview version of the Microsoft.Azure.AppConfiguration.AspNetCore package there are some differences that you need to know because how we need to use Managed Identities with App Configuration has changed since there are some changes to the Microsoft.Extensions.Configuration.AzureAppConfiguration library. We used AzureAppConfigurationOptions.ConnectWithManagedIdentity() method to access App Configuration with managed identity. But now the AzureAppConfigurationOptions.Connect() method has an overload that accepts a Uri endpoint and a TokenCredential instance to use different ways to access Azure resources. And this include the use of Managed Identities with ManagedIdentityCredential implementation. This change is coming from the use of Azure.Identity library and you need to add this NuGet package to get access to these TokenCredential implementations.
Install Azure.Identity NuGet package and update the Microsoft.Azure.AppConfiguration.AspNetCore NuGet package to the latest preview version
Install-Package Microsoft.Azure.AppConfiguration.AspNetCore -Version 3.0.0-preview-011100002-1192
Install-Package Azure.Identity -Version 1.1.0The updated the code in the Program.cs file to the following.
using Azure.Identity;
namespace MusicStore.Web
{
public class Program
{
...
public static IHostBuilder CreateHostBuilder(string[] args) =>
Host.CreateDefaultBuilder(args)
.ConfigureWebHostDefaults(webBuilder => {
webBuilder.UseStartup<Startup>();
})
.ConfigureAppConfiguration((context, config) => {
var settings = config.Build();
var appConfigEndpoint = settings["AppSettings:AppConfiguration:Endpoint"];
if (!string.IsNullOrEmpty(appConfigEndpoint))
{
var endpoint = new Uri(appConfigEndpoint); // Create the endpoint object of type Uri
config.AddAzureAppConfiguration(options =>
{
options
.Connect(endpoint, new ManagedIdentityCredential())
.UseFeatureFlags();
});
}
});
}
}Here without supplying the connection string for the App Configuration instance, we are using a different overload of the Connect() method by supplying the URL to the App Configuration instance as a Uri type and also using a new ManagedIdentityCredential object. That is, it in terms of the code changes you need to do. But there are some other changes that is needed to be done in the Azure Portal. Let’s look at that.
Enable System Assigned Managed Identity in Azure App Services
We are deploying our Music Store application on to an Azure App Service instance. And App Services support the use of Managed Identities.
Go to the Identity under the Settings section of the App Service instance and under System Assigned you need to flip the toggle button to On and click Save. Accept the dialog box to confirm the use of System Assigned managed identity.
And finally, you need to do a Role Assignment to Azure App Configuration instance by adding the System Assigned Managed identity.
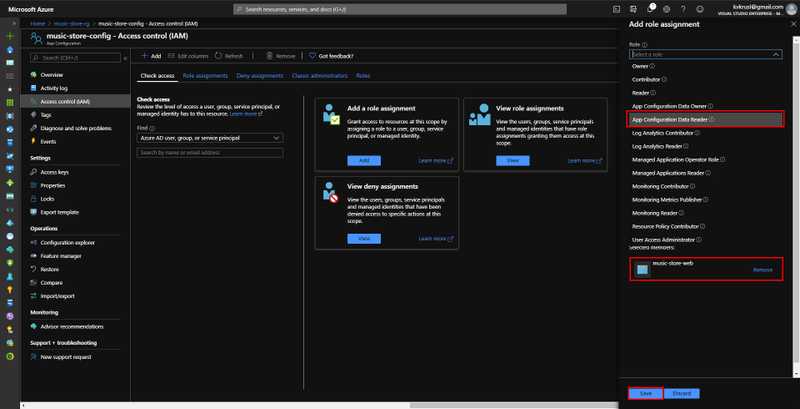
Go to the Azure App Configuration instance and then to Access Control (IAM) there click on Add and select Add Role Assignment.
You need to select the App Configuration Data Reader role from the Role Dropdown and then Select the System Assigned Managed Identity we enabled. This will have the same name as the App Service. Once you select the role and the identity click on Save to confirm the changes.
Now if you publish the application and run it on the App Service instance you will see that the Music Store application is able to access the discount value of 20% from the App Configuration’s configuration management and also access the feature flags defined in App Configuration Feature Management.
Using User Assigned Managed Identity to Access App Configuration
Create a User-Assigned Managed Identity in the Azure Portal. The creation process is simple, We will use this identity to access the Azure App Configuration.
Once the identity created, you need to copy the Client ID of the newly create managed identity and add it to the App Settings of the Azure App Service. Let’s use the Key AppSettings:Identity:ClientId and add the Client ID. The client id can be found in the overview section of the User-Assigned Managed Identity
Then you need to go to the Identity under Settings section and then switch to User-assigned and add the user assigned managed identity we created.
Finally, all you need to do is change the code in the Program.cs a little bit to support the use of user-assigned managed identity. Look at the example below.
using Azure.Identity;
namespace MusicStore.Web
{
public class Program
{
...
public static IHostBuilder CreateHostBuilder(string[] args) =>
Host.CreateDefaultBuilder(args)
.ConfigureWebHostDefaults(webBuilder => {
webBuilder.UseStartup<Startup>();
})
.ConfigureAppConfiguration((context, config) => {
var settings = config.Build();
var appConfigEndpoint = settings["AppSettings:AppConfiguration:Endpoint"];
var userAssignedIdentityClientId = settings["AppSettings:Identity:ClientId"];
if (!string.IsNullOrEmpty(appConfigEndpoint))
{
var endpoint = new Uri(appConfigEndpoint);
config.AddAzureAppConfiguration(options =>
{
options
// Provide the client id of the User-Assigned Managed identity
.Connect(endpoint, new ManagedIdentityCredential(clientId: userAssignedIdentityClientId))
.UseFeatureFlags();
});
}
});
}
}All we have done here is to retrieve the Client ID of the user-assigned managed identity from the Configuration and then supply the Client ID parameter into the ManagedIdentityCredential object. That is it. Now if you publish the application and try running application, you can see the application is running and the app configuration and feature flags are retrieved from Azure App Configuration.
Summary
In this article we looked at what has changed in the latest versions of the preview packages of Microsoft.Azure.AppConfiguration.AspNetCore and Microsoft.Extensions.Configuration.AzureAppConfiguration packages. And how we can use Azure Managed Identities to access Azure App Configuration without having to manage secrets and connection strings ourselves. In upcoming articles, we will look at some of the advanced usages of Azure App Configuration. The sample code can be found on the Azure App Configuration Managed Identity Example GitHub repository.
Tags:
You Might Also Like
← Previous Post