Resource Governance and Compliance with Azure Policy

When you are working in an organization that has to comply with different regulations with regards to your cloud infrastructure and resources, it can be a headache to manage these especially if you have a large amount of cloud resource to manage. If you are working with Azure, Azure Policies can help you immensely with these Governance and Compliance requirements. Let’s look at what Azure Policies are and how to use them.
What is Azure Policy?
Azure Policy is a service that Azure provides to govern your Azure Resources by creating, assigning and managing different policies. With the use of these policies you can enforce different rules over your Azure Resources and make sure these resources are compliant with your organizational and other standards you are following.
Once you have created or assigned policies to Azure Resources, these resources are periodically evaluated against the policies you have and if there are any resources that does not comply with the policies, they will be flagged as Non-Compliant and you can take action on them. When a policy is implemented both New and Existing resources are affected. And these effects on the resources are determined by the Effect the Policy Definition has. For example, you can just Audit a compliance violation or you can completely Deny a violation, meaning preventing a resource from being created.
We will look at how to create your own Policy Definitions in a later article. In this article we’ll look at what are some of the built in Policy Definitions and How you can apply them. Before that, some more terminology.
Policy Definitions
Policy Definition is basically a rule that has one or more conditions under which it’s enforced. Also these definitions has an effect that dictates what action will be taken when the conditions are met. There are number of built-in Policy Definitions you can choose from and you can create your own Policy Definitions as well. These Policy Definitions can be created using JSON.
Policy Assignment
Policy Assignment happens when a Policy Definition is assigned to take effect with a specific Scope. The scope can be a Management Group, a Subscription or even a Resource Group. Once a Policy Assignment is created for example for a Resource Group that assigned policy will be inherited to all the child resources in the resource group as well. And they will be evaluated against the assigned policy.
What are Initiatives?
An initiative or Initiative Definition is a collection of policy definitions that are grouped to achieve a single compliance goal. If you have multiple Policies that you have to assign to comply with a certain requirement its much easier to create an Initiative Definition with those Policy Definitions and create an Initiative Assignment.
An Initiative Assignment is just like a policy assignment where you are assigning a Initiative Definition with a specific scope.
Since now we have a basic understanding of what Azure Policies are, the terminology and how we can use them, Let’s see how we can create Policy Assignment using Azure Portal, Azure PowerShell and Azure CLI
Creating a Policy Assignment using Azure Portal.
To create a new Policy Assignment, we will use a build-in Policy Definition. To do this go to Azure Policy by either Searching in the top search bar or from the left Navigation menu. Then on the Policy blade, click on Assignment menu item to see the current assignments and to create new Assignments.
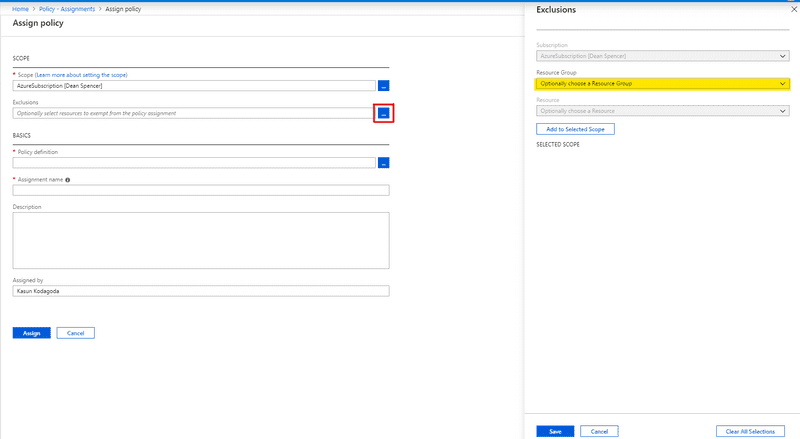
Click on Assign Policy and you will see a new blade to create a new Policy Assignment. In the Assign Policy blade, you can select the Scope of the policy assignment, any Exclusions you may want to add, select a Policy Definition from all the available Policy Definitions, add a Name and a Description for the Policy Assignment.
Click on the button next to the Scope and you can select the scope of your Policy, Select the Subscription and if you want to scope it to a Resource Group, you can select an existing Resource Group as well. Finally, click Select to confirm the selection
If you want to add any Exclusions by selecting any Resources or Resource Groups from the Policy assignment, you can add them here
By clicking on the button next to Policy Definition, you can select from the available built-in policies as well as custom policies. You can filter by the Type or Search for a policy. I will Search and select Allowed Locations policy. And select it.
Once you select the Allowed Locations policy, Policy name will be automatically filled, but you can change this as well. Next there will be additional inputs shown depending on what policy you selected. Here you are shown a Location Selection list and you can select the locations to allow. I’ve selected Australia East for this example.
Finally, you can click on Assign to complete the Policy Assignment.
It will take up to 30 mins to 1 hour to run the Policy evaluation and the compliance info to show up. Next, we’ll quickly create 2 more Policy Assignments using Azure PowerShell and Azure CLI
Creating a Policy Assignment using Azure PowerShell
We will be using Azure PowerShell to create a Policy Assignment scoped to a Resource Group. I have a resource group created with the name az-policy-rg. Following script will create the policy assignment.
# Login to Azure Subscription
Login-AzureRmAccount
# Get a reference to the resource group
$rg = Get-AzureRmResourceGroup -Name "az-policy-rg"
# Get a referecen to the Azure Policy Definition
$policyDef = Get-AzureRmPolicyDefinition | Where-Object { $_.Properties.DisplayName -eq "Audit VMs that do not use managed disks" }
# Create the new Policy Assignment for the Resource Group
New-AzureRmPolicyAssignment -Name "Check for Managerd Disks" -DisplayName "Check for Managed Disks" -Scope $rg.ResourceId -PolicyDefinition $policyDef
Here we are assigning Audit VMs that do not use managed disks policy to the resource group. I’m using Get-AzureRmPolicyDefinition command to get all the Policy Definitions and selecting the specific Definition we want.
Also, I’m using Get-AzureRmResourceGroup command to get a reference to the resource group.
Finally, I’m using New-AzureRmPolicyAssignment command with the Scope assigned to the resource group reference we got earlier.
Creating a Policy Assignment using Azure CLI
We now assign a new Policy to the same _az-policy-rg_ resource group, this time using Azure CLI. We’ll assign Audit use of classic virtual machines policy.
# Login to Azure
az login --use-device-code
# Get Reference to Resource Group
$rgId = az group show --name "az-policy-rg" --query "id" --output tsv
# Get Reference to the Azure Policy Definition
$policyName = az policy definition list --query "[?displayName == 'Audit use of classic virtual machines'].name" --output tsv
# Assign the policy
az policy assignment create --name "Check for Classic VMs" --display-name "Check for Classic VMs" --policy $policyName --scope $rgIdJust as before, we are getting a reference to the resource group ID using JMESPath query provided with the —query parameter. Next, we are getting a reference to the policy Definition Name, which is a unique ID by again using JMESPath query.
Finally, we are creating the policy assignment with the policy Name and resource group ID as the scope.
Conclusion
In this article we looked at what Azure Policy is and where and how we can use them and then created Azure Policy Assignments using Azure Portal, PowerShell and Azure CLI. In follow up articles we’ll look at how to create custom Policy Definitions and creating Initiative Definitions and assigning them to different scopes.
You Might Also Like
← Previous Post