Automated Security Testing with OWASP Zed Attack Proxy: #1 Installing & Configuring OWASP ZAP on an Azure Virtual Machine

OWASP Zed Attack Proxy (ZAP) is a free security tool that helps you automatically find security vulnerabilities in your web applications. It is one of the most popular tools out there and it’s actively maintained by the community behind it. It’s a great tool that you can integrate while you are developing and testing your web applications.
In this series of posts, we’ll look in to how to install and configure OWASP ZAP on an Azure Virtual Machine and expose its API so we can automate our security testing and integrate it into our Build/Release pipelines. First, we need to create an Azure Virtual Machine and install OWASP ZAP on it.
Create the Azure Virtual Machine
Log in to Azure Portal and search for Virtual Machine resource to create a Virtual Machine. We’ll create a Windows 2016 Data Center Virtual Machine with a managed disk as the OS disk. You need to also need to add Inbound Rules for HTTP and HTTPS into your Network Security Group (NSG) so we can access the sites hosted in the VM later. You can find more details on how to create the VM with the relevant configurations in one of my previous articles on Installing & Configuring SonarQube using Azure Virtual Machines and Azure SQL.
After creating the Virtual Machine, connect to the VM by downloading the RDP file from the Portal. Then you need to install Java Runtime Environment 8 so that OWASP ZAP can be run on the Virtual Machine.
Installing OWASP Zed Attack Proxy (ZAP)
After installing Java Runtime Environment 8 on the Virtual Machine, download OWASP ZAP from the GitHub Wiki Download Page. Run the installer and accept the default configuration and follow the instructions to install OWASP ZAP.
After the installer is complete, you will see a shortcut created for OWASP ZAP on the desktop. Double click on the shortcut and open ZAP. It will take a few seconds to open up and then you will be presented with a dialog to select options to persist the ZAP Session. Select “No, I don’t want to persist this session at this moment in time” option since we are not doing anything at the moment and click Start Button.
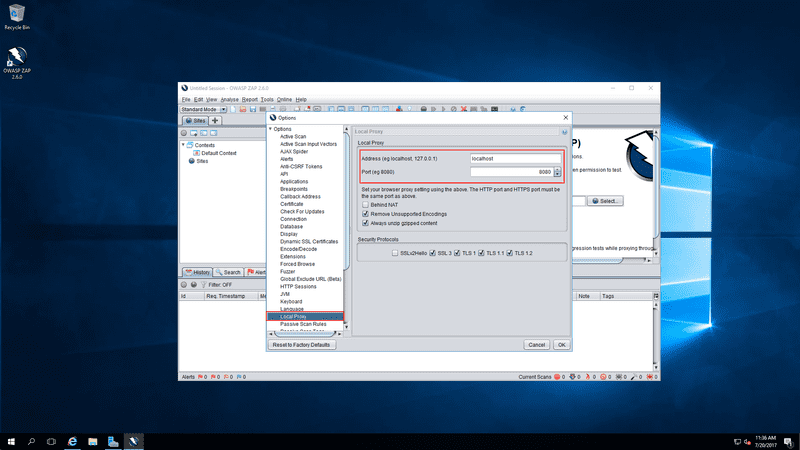
On the ZAP window, on the menu bar click on Tools > Options, the options dialog will open up.
Then in the open dialog, click Local Proxy on the left menu and see the options for the local proxy. The local proxy will be running on localhost port 8080 by default. You can change this if you want.
Now if you navigate to a browser instance and go to http://localhost:8080 you can see the OWASP ZAP proxy is running and that means the API is available.
But if you close the OWASP ZAP application, then the local proxy will not be available. Close the ZAP application and try to refresh the local proxy page.
To get over this issue, we’ll have to run ZAP in the daemon mode. We’ll create a .bat file and add a shortcut to Windows Startup so every time the VM restarts, the daemon will be up and running and ready to accept API calls.
Running OWASP ZAP in the Daemon Mode
Create a .bat file and include the following command into the .bat file.
start /d "C:\Program Files\OWASP\Zed Attack Proxy" zap.exe -daemon -host localhost -port 8080The start command executes the zap.exe with the -daemon argument with -host as localhost and -port as 8080 as the other arguments. Since we do not want to change the host and port having only -daemon argument would do. But here we are supplying the -host and -port to demonstration purposes. I saved the .bat file to the root of the C: partition.
Then right click on the .bat file and drag it to the desktop to create a shortcut. Then we need to add this shortcut to the Windows Startup. Press Windows + R keys to open run dialog and enter shell:startup and click ok to open up the Startup directory.
Then move the shortcut to the Startup directory and next time the server starts the ZAP daemon will start and the Local proxy is available even if the ZAP application is closed. Run the .bat file to start the ZAP daemon and navigate to http://localhost:8080 and you will see that the proxy is running.
Configure the Reverse Proxy to Expose the API
To access the ZAP API from the outside we need to expose the proxy running locally via a reverse proxy. To do this we need to install Internet Information Services (IIS) on the windows server and also add 2 IIS Extensions on it. We need to install URL Rewrite Extension and Application Based Routing Extension on IIS.
Then we need to create a Self-Signed Certificate to allow encrypted communication with the ZAP API (if you want to do so) and add the necessary HTTP and HTTPS bindings to the IIS Website we are going to create. This is a somewhat lengthy process, but no need to be worried. In one of my previous articles describing exposing SonarQube over SSL to the outside world, I have gone into quite a lot of detail on how to do this. The steps are exactly the same. (only change is we will be using the port 8080).
Read Configuring SSL for SonarQube & Securing the SonarQube Server Behind a Reverse Proxy article and follow the steps to expose ZAP API over the internet. In that article, I explain how to;
- Installing IIS & the Required Extensions
- Creating the Self-Signed Certificate
- Enabling Proxy and Adding the URL Rewrite Rule
- Adding an A Record (or a CNAME Record)
After you set up the reverse proxy you will be able to access the ZAP API over the internet.
Now you are all set to use the OWASP ZAP to run automatic security tests. In the next article, we’ll discuss how to use a Visual Studio Unit Test project and Use OWASP ZAP .Net API NuGet package to access the ZAP API we exposed to run the security tests. Then we’ll use Visual Studio Team Services to include the Security Test runs in Build/Release Pipeline. I’ll see you in the next one.
Automated Security Testing with OWASP Zed Attack Proxy - All Articles
- #1 Installing & Configuring OWASP ZAP on an Azure Virtual Machine (This Article)
- #2 Creating & Running Automated Security Tests on Visual Studio Team Services
- #3 Working the Result of ZAP Security Scan to Pass or Fail the Security Tests
You Might Also Like
← Previous Post